Office 365 configuration best practices
I try with this blog to present you the minimum you need to do for the Office 365 configuration best practices.
Office 365 account takeover
Office 365 account takeovers are really problematic when it comes down to Office 365 attacks. The most interesting targets are of course tenants without the MFA setup for the GA (global admin), because brute force over period of time can allow unauthorized user to gain access to your Office 365 tenant. There is no worse nightmare for the user but losing their Office 365 tenant.
How usually this happens?
The most popular method today is phishing. Phishing is very dangerous method where basically remote attacker gains access to the Office 365 tenant. I have seen multiple examples I will show you few
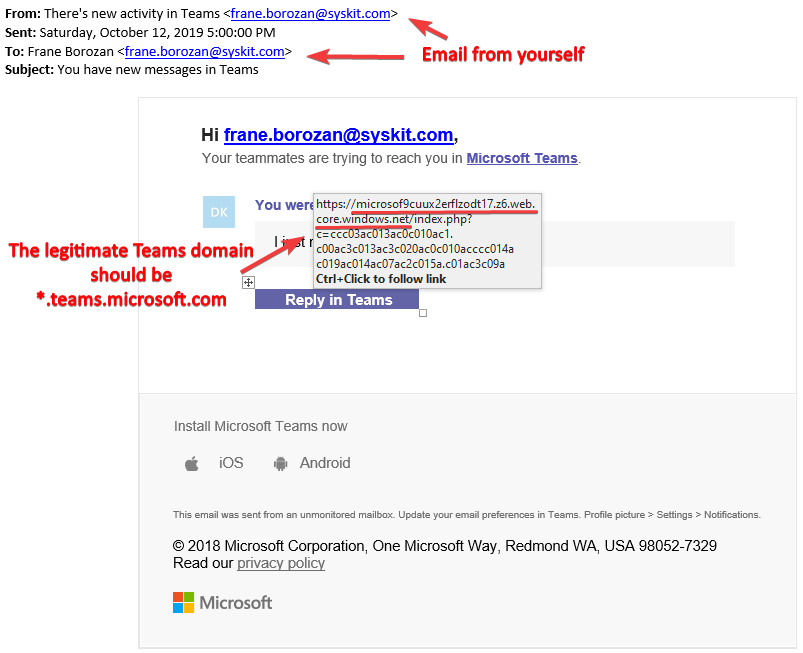
teams phishing where remote attacker tells you that you have a new message in teams, so you need to sign in and check it.
phishing that comes from Microsoft Planner
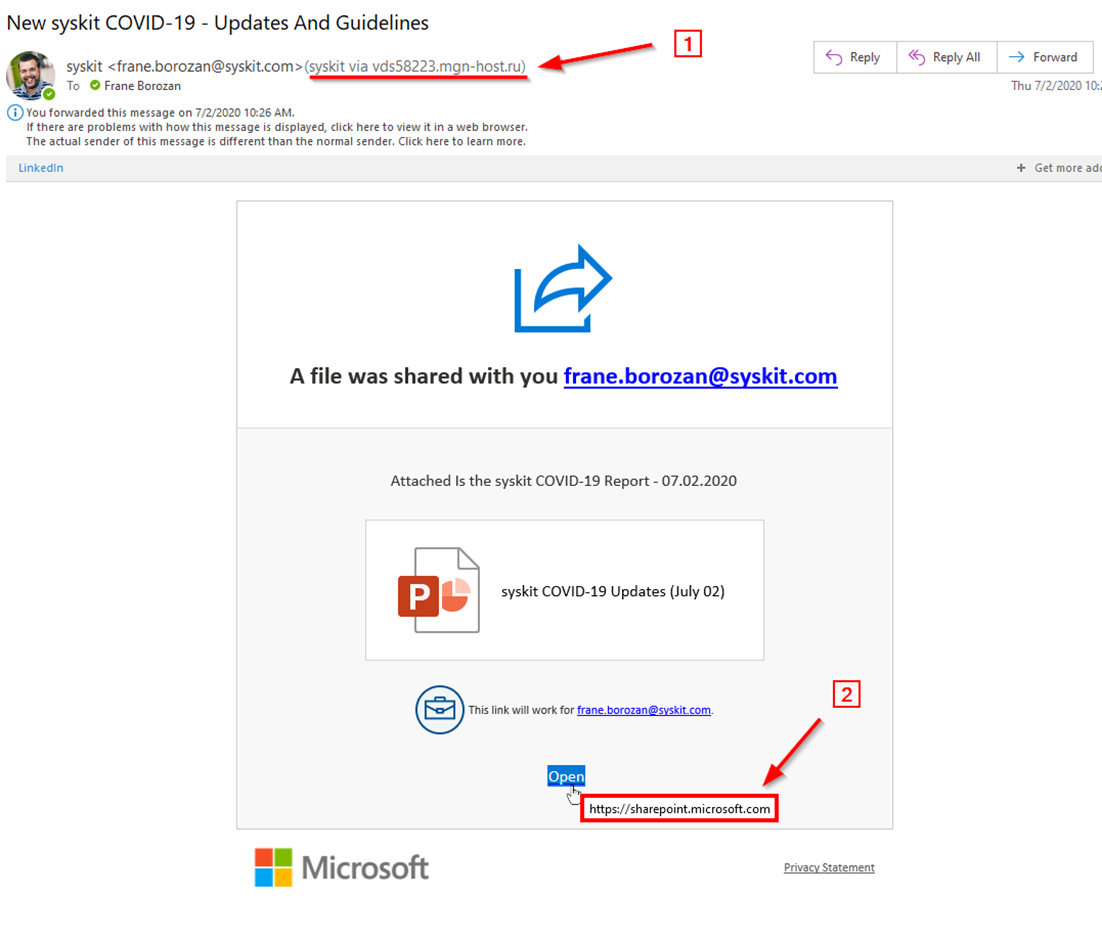
popular lately where Covid 19 is used in the keywords. A lot of companies choose to communicate with their employees and remote attackers are using this because they know some of the frightened people will click on the link.
To see any of this files first you need to login to the link, and then you will have access to the file.
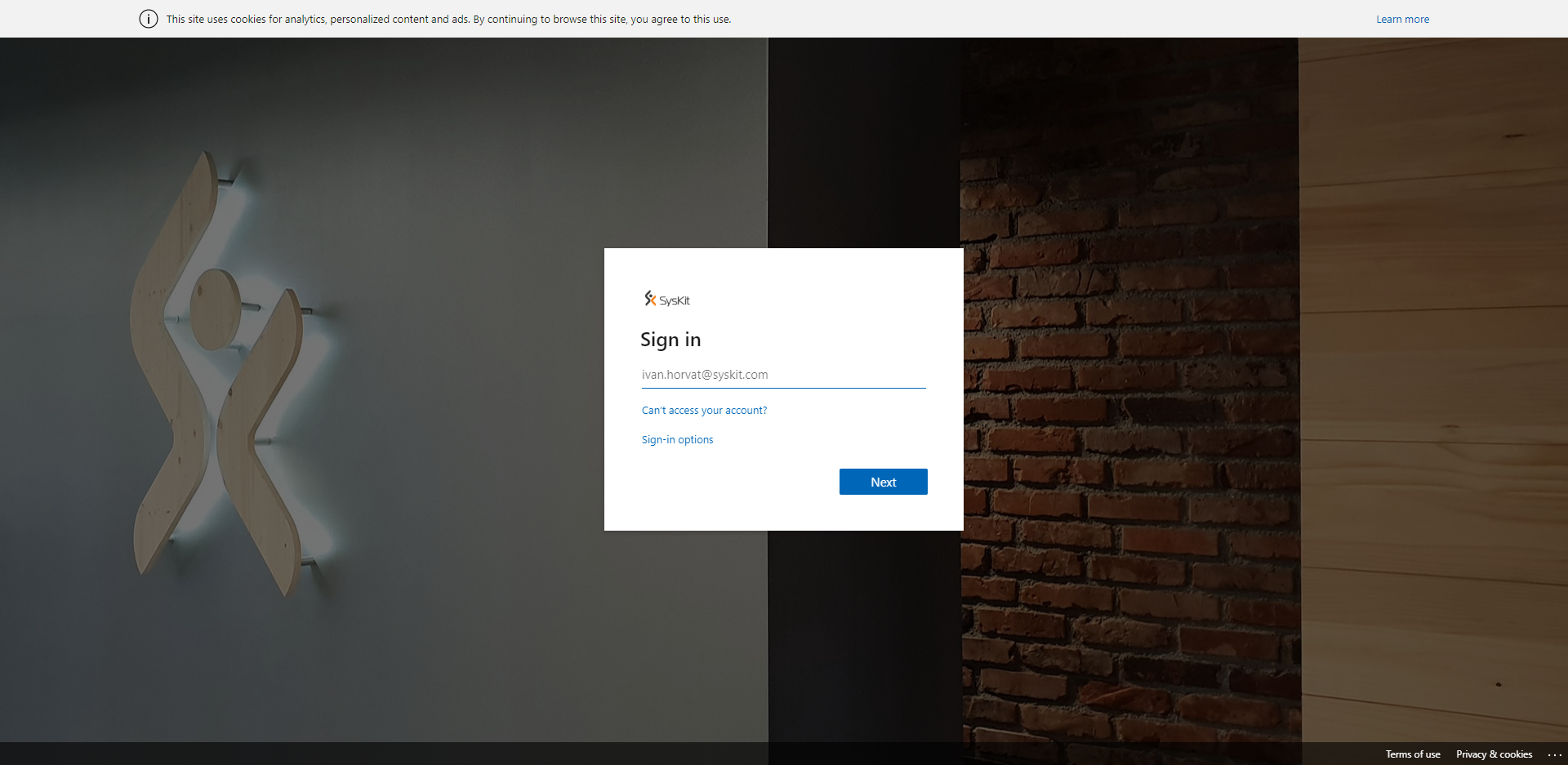
I recommend using custom background that is specific to your company. For example put your company logo where users can recognize it and they will know this is their company.
What I saw is a lot of company are not changing this background to reflect their company logo, so their user won’t feel he is entering login details to the wrong site.
below is example of the login in our company. This logo is on the very entrance in our company, and it is on the entrance to the Office 365 as well so our employees will know this is legit Office 365 login page.
When account takeover kicks in the attacked probably won’t do a thing for quite some time. He will start watching you mailbox and remote attacker will try to understand who is the most important user in your environment. For example global admin user will take attacker for the possibility to control the complete tenant. Finance user is receiving invoices to be paid, remote attacker can easily change the account number or the IBAN on the invoice and steal a large amount of money before the company understand what can happen. And you won’t know a thing that somebody is in your environment!
How to configure your tenant to prevent security breaches and have Office 365 configuration best practices
To reduce possible of this attacks there are few steps that can help you in this scenarios.
- require multi factor authentication for all the users in the company, and specially global admins
- limit remote access protocol for the email
- use conditional access if possible
- do check secure store and what needs to be improved there https://security.microsoft.com/securescore
- manage forwarding of the emails
- have mailbox auditing and changes over mailbox in your process so you understand if mails are being forwarded outside the company
- turn on audit logging if you haven’t already, this is required to understand what is going on with the tenant. by default in the E3 license you have 90 days of the audit logs and in the E5 license you have 365 years of the audit log so your can go back if you had a breach and understand what happened
1. Require multi factor authentication for all the users in the company, and specially global admins
Usually the first and most important thing you can do to protect your tenant is MFA for everybody who are consuming the tenant.
Before you begin make sure you have:
- GA rights, only GA can manage MFSA
- if you have legacy per person MFA, disable it first
- If you have Office 2013 first turn on modern authentication
- if you have ADFS setup the Azure MFA server
More details about multi factuor auth are available here: https://docs.microsoft.com/en-us/microsoft-365/admin/security-and-compliance/set-up-multi-factor-authentication?view=o365-worldwide
2. Limit remote access protocol for the email
Are you using POP3, IMAP, MAPI, EWS, OWA, and ActiveSync for every system user. Probably not, if you are not using this protocols disable those. If you users are not using POP3 or IMAP (and in the era of the Office 365 I highly doubt they use anything else but the ActiveSync) disable it. The less protocols you have exposed outside the less options you are leaving to the attackers.
3. Use conditional access if possible
Conditional access is a huge PITA, but if configured correctly it is a huge security benefit to the company. Basically it brings multiple signals together to make decisions if user access will be allowed and then based on the company policies it will allow or block access to the user.
Conditional access is available only for Azure AD Premium P1, or licenses that include this, such as Microsoft 365 Business Premium, and Microsoft 365 E3.
More about conditional access here https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
4. Do check Secure Score and what needs to be improved there
Secure store is analytics tools that is inspecting your tenant and shows you the best practices for the Office 365 and what you could do about it. Secure store for all tenants is available here: https://security.microsoft.com/securescore
5. Manage forwarding of the emails
if somebody manages to gain access to the emails of your users first thing they will setup email forwarding to the external user address so he doesn’t need to login every once in w awhile to the mailbox and check the messages (login to the email also generates logon event and admin can see that somebody is logging on from Vietnam for example, and could alert him). So pay attention to the mail rules and check regularly logs of your EXO.
From an administrative perspective, you can configure O365 to alert you if a user sets up a new inbox rule. It is easy setup through alert policy’s in the security and compliance center https://protection.office.com/alertpolicies
There is an excellent blog by Microsoft to determine accounts that have forwarding enabled: https://docs.microsoft.com/en-us/archive/blogs/timmcmic/office-365-determine-accounts-that-have-forwarding-enabled
6. Enable mailbox auditing and revise changes over mailbox in your process
Mailbox auditing should also be a part of your security process where you need to examine EXO audit logs, and understand if somebody has changed mailbox permissions. All the mailbox changes are ending up in the Office 365 audit log so from the Security & Compliance Center.
Microsoft is in the process of turning auditing by default but until then you need to enable it. You must first turn on audit logging before you can start searching the audit log. To turn it on, click Turn on auditing on the Audit log search page in the Security & Compliance Center. (If you don’t see this link, auditing has already been turned on for your organization.) After you turn it on, a message is displayed that says the audit log is being prepared and that you can run a search in a couple of hours after the preparation is complete. You only have to do this once.
Mailbox auditing starting Jan 2019 is enabled by default for all organizations so you don’t need to manually enable it for new users.
7. Turn on Office 365 audit logging if you haven’t already
This is directly connected with the previous point. Don’t only audit mailboxes, but audit the complete Office 365 tenant.
When audit log search in the Security & Compliance Center is turned on, users and admin activity from your organization is written in the audit log and retained for 90 days for the E3 license, or 1 year for the E5 license (there is also special E3 licenses Compliance licenses that allows 365 days of the audit logs, so please consult with Microsoft for this periods).
Tools to manage configuration changes and Office 365 tenant settings
There are a lot of different settings in the Office 365 configuration and sometimes you are not sure where exactly is that specific setting, or if that setting has changed in the past. I can recommend for this 3rd party product SysKit Trace for documenting Office 365 and track configuration changes. Product is available here https://www.syskit.com/products/trace

If you need a test license, or your are a Microsoft MVP get in touch with me directly https://www.lemonbits.com/contact-me/