Intro
SharePoint audit logs allows your organization to see who is accessing what files and folders, site collection, sites and subsites, document libraries, lists or list items you name it. In case you need to audit who did what on the SharePoint site for various reasons like for the compliance projects like GDPR, for the external auditor, tax audits or just because your organization policy is to audit everything you don’t need to look anywhere else. In today blog I will cover what is auditing on the SharePoint, where you need to enable it, and how to automate auditing to be enabled on all the SharePoint site collections within your farm (basically the reason to write this blog post is because of that, I was not able to find how to enable for all site collections on the SharePoint farm).
The article was built for SharePoint 2016 but I believe it works on SharePoint 2013 and SharePoint 2019 auditing works the same as well. If something is changed meanwhile please let me know in the comments below.
Where to enable Audit Settings on the farm level
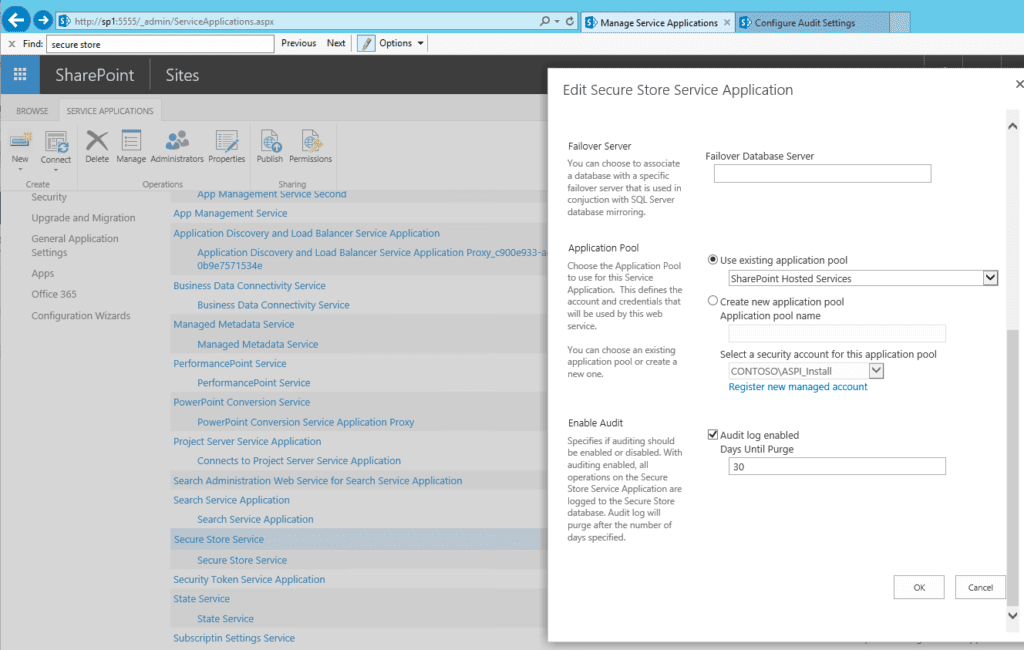
- Go to the Central Administration
- Go to Application Management then Manage Service Aplications
- Select the Secure Store Application
- On the ribbon, click ‘properties’
- In the ‘enable audit’ section; click to select the audit log
- To change the number of days that entries will be purged from the audit log, specify a number in days – default is 30
Where to configure audit settings for the site collection
You need to go to site settings > site collection audit settings.
There we can configure multiple stuff.
Audit Log Trimming
If you want to automatically trim audit log and after how log you can trim it here. The first setting enables trimming and second allows you to configure after how log to trim the log. If you leave it empty it will use the farm setting. Default end of the month means the change log retains data for 60 days. That means then logs will retain for two months. Recommended is not to set this setting on the site collection but to use the farm wide setting.
Documents and Items and Lists, Libraries, and Sites
Now we need to to set events to audit for various types. Following events are available:
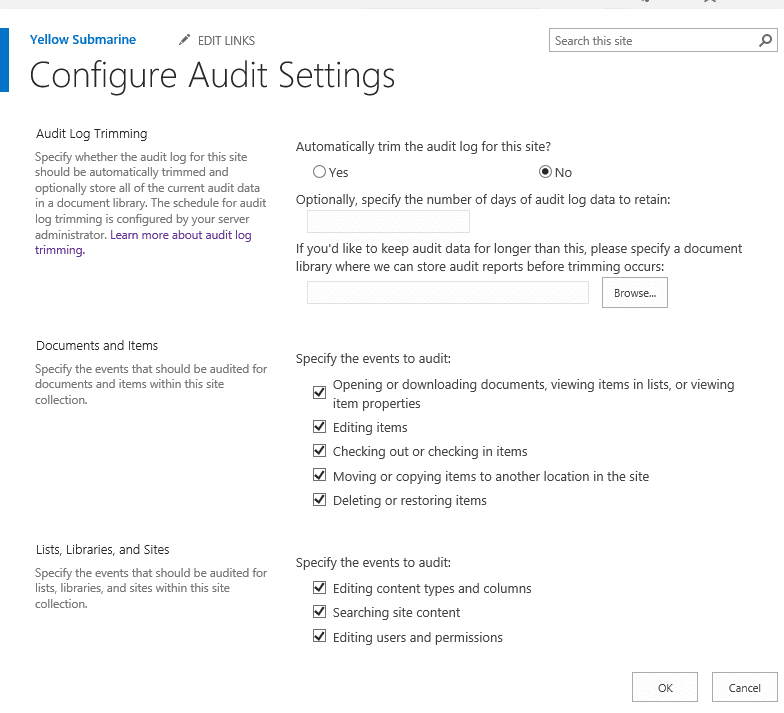
- Opened and downloaded documents, viewed items in lists, and viewed item properties (BTW N/A for SharePoint Online sites)
- Edited items
- Checked-out and checked-in items
- Items that have been moved and copied to other locations in the site collection
- Deleted and restored items
- Changes to content type and column
- Search queries
- Changes to user accounts and permissions
- Changed audit settings and deleted audit log events
- Workflow events
- Custom events
Depending on what you need to audit you can enable partially settings, but usually people want to audit everything so let’s check all the boxes.
FYI you need to be careful with the first option on the huge farms. Opened and downloaded documents, viewed items in lists, and viewed item properties can cause quite a lot impact on the SQL server and the size of the table where SharePoint is storing the logs.
Every SharePoint environment is different any you need to track how your database grows over time and if you can support this amount of logs.
PowerShell to enable all audit settings on all site collections
So manually enabling auditing on each collection would be PITA, because you need to manually go to each site collection, open site collection audit settings and click all 8 check-boxes. That is the reason why I have created a PowerShell that discover all the site collections and enables all auditing on all of them.
FYI I’ve seen farms with as much as 200k+ site collections so imagine if you need to do this manually :D
This PowerShell will run with elevated privileges and on all SharePoint site collections will enable all the auditing settings.
[Microsoft.SharePoint.SPSecurity]::RunWithElevatedPrivileges(
{
$sites = Get-SPSite -Limit All
foreach($site in $sites)
{
$site.Audit.AuditFlags = $site.Audit.AuditFlags = [Microsoft.SharePoint.SPAuditMaskType]::CheckOut `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::CheckIn `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::View `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::Delete `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::Update `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::ProfileChange `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::ChildDelete `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::SchemaChange `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::SecurityChange `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::Undelete `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::Workflow `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::Copy `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::Move `
-bxor [Microsoft.SharePoint.SPAuditMaskType]::Search
$site.Audit.Update()
$site.Dispose()
}
})
Where to View and Generate SharePoint Audit Logs Reports
When you have configured audit logs you can find them in Site Settings > Audit Log Reports.
Once you configure the audit logs you can view them in Site Settings. Under Site Collection Administration you will find the Audit Logs Reports option. This is really simple you just need to select what type of the audit events want and SharePoint will generate excel file for you.
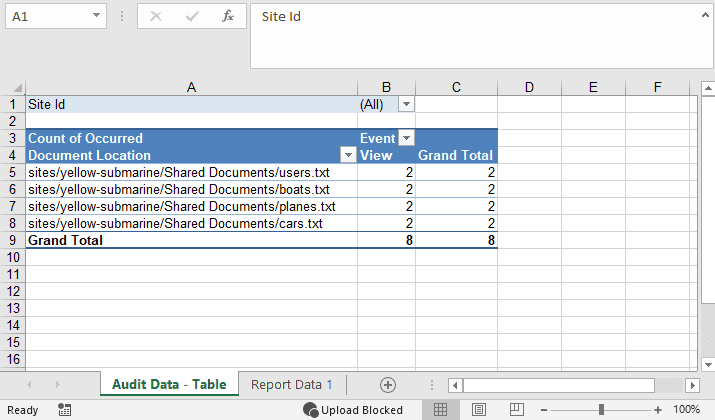
In the file you will have two sheets, the first will be the count of the event your selected for all the documents and on the second screen you will have all the users that accessed the document. Plain and simple.
The PITA is that you need to do this for every different event and for every site collection so that can be again time consuming.
PowerShell to automate viewing audit logs from all site collections
So manually generating excel files for each site collection is a lot of the manual job so I decided to ease your life with the PowerShell.
Add-PSSnapin Microsoft.SharePoint.Powershell -ErrorAction SilentlyContinue
[Microsoft.SharePoint.SPSecurity]::RunWithElevatedPrivileges(
{
$sites = Get-SPSite -Limit All
foreach($site in $sites)
{
$auditQuery = New-Object Microsoft.SharePoint.SPAuditQuery($site)
$auditLogs = $site.Audit.GetEntries($auditQuery)
foreach($logEntry in $auditLogs)
{
$user = $site.RootWeb.SiteUsers.GetByID($logEntry.UserId).Name
Write-Host "Document: " $logEntry.DocLocation " Event: " $logEntry.Event " User: " $user " Details: " $logEntry.EventData
}
}
})
This is example that I generated on my test farm for all the site collections:
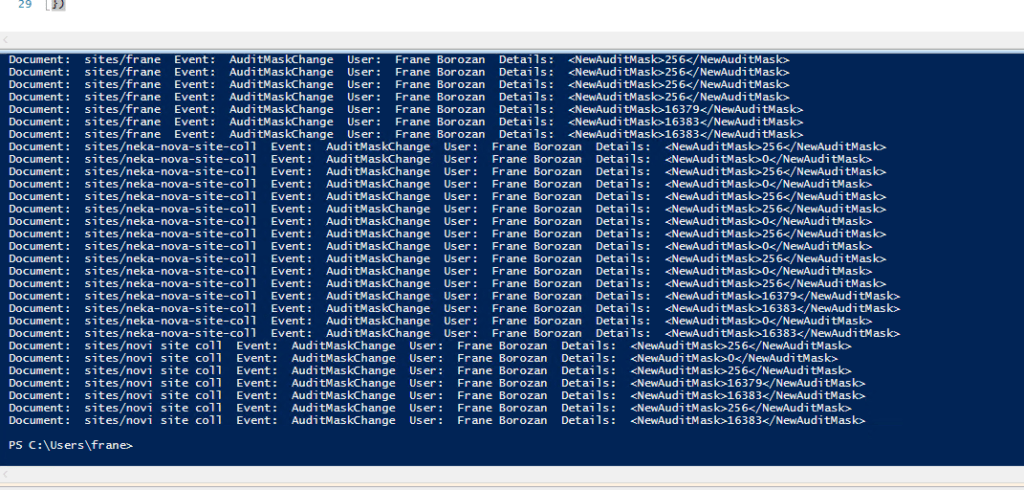
SharePoint audit logs
I hope you guys now understand how to set audit logs on the farm wide level and for each site collection out there. Let me know in the comments below what do you think about it and how do you audit your farm.
BTW if you want professional looking solution, where you can manage multiple SharePoint farms audit logs, and you want exportable report that is professional looking you want to look at the SPDocKit solution. SPDocKit is easily installed and you can use it to offload your audit logs from the farm and keep logs for longer periods. When you offload the logs, the audit table will be a lot smaller and if you need to search thru the audit logs, or provide access to the auditor from few months ago you can use the SPDocKit because it will hold the logs practically forever. 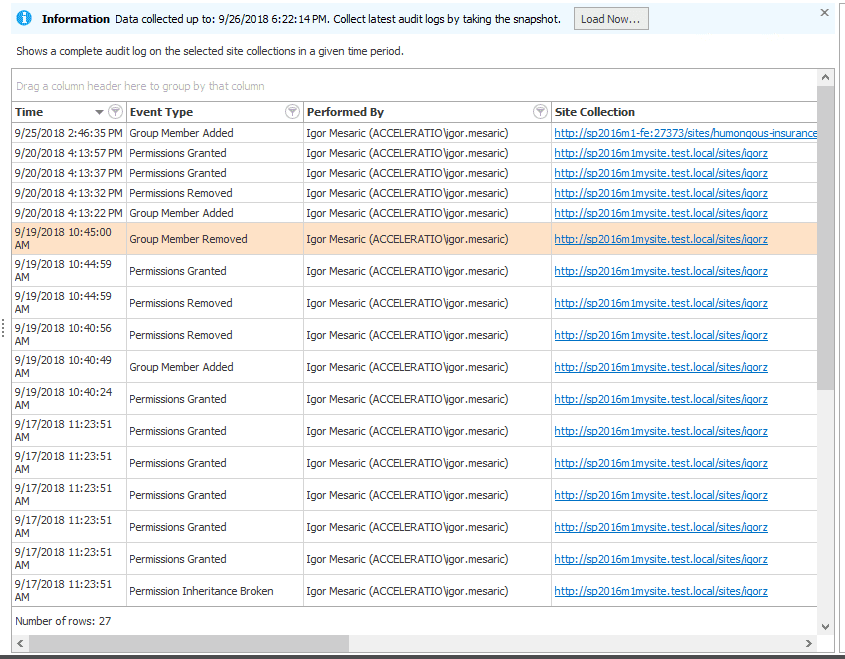


5 Responses
It does NOT work the same fpr SP2019. The first checkbox “Opening or download…” is removed from the GUI.
The auditlogging for SP2019 doesn’t work the same as 2013 and 2016. The ability to aduit access to a file (read) has been removed by Microsoft. You can turn it on by code (and it will generate data) but it is acording to premier support from Microsoft NOT supported.
HI, thanks for the script.
had a question, in “PowerShell to enable all audit settings on all site collections” i want to enable audit trimming and save the logs to a location on the site collection. how do i do that?
great post.
how do I generate a list of sites that have auditing enabled already. want to maintain a record of the sites and settings before i enable on all the sites.
thanks for your help
Currently the Audit Log Trimming is set to run monthly basis. I need to switch it to weekly. But before that I need to know what is the impact of the same to the farm?