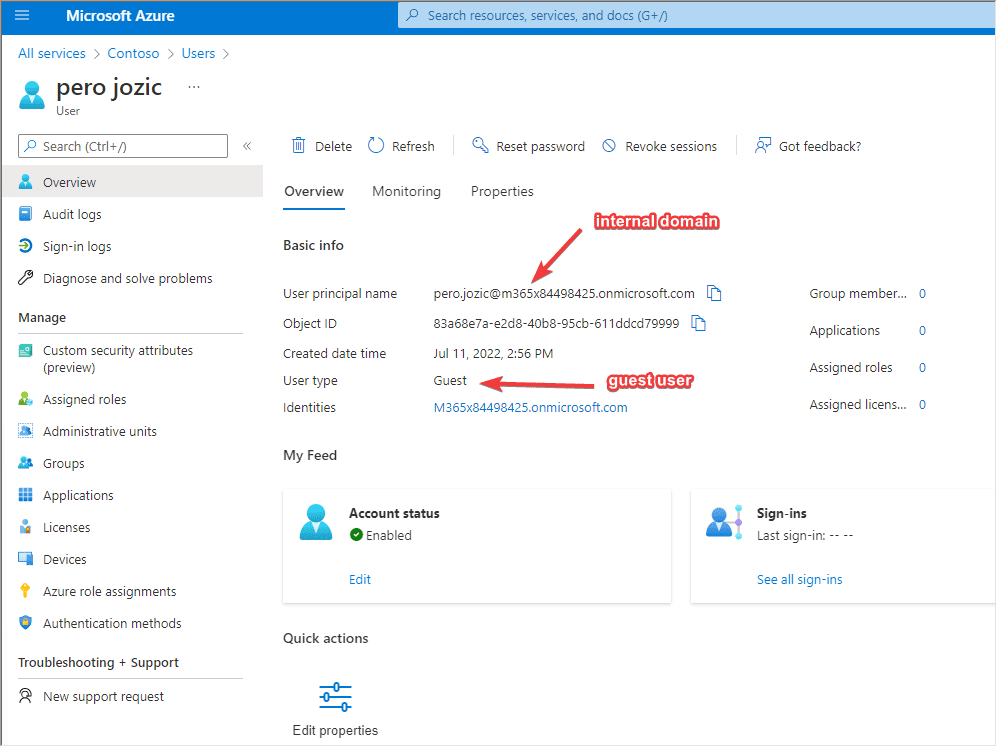
Did you know you can have an internal guest user? To be honest, I haven’t ever used an internal guest user, I would always use an internal account with fewer privileges (meaning giving access only to resources the account needs to have access to).
There are for types of the UserType property in the Azure AD:
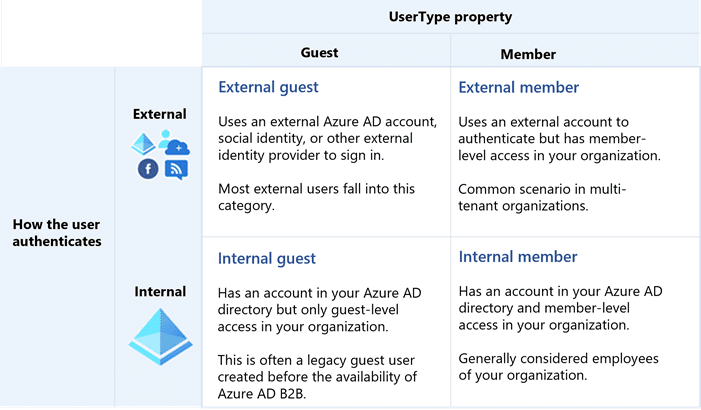
- External guest (external Azure AD account, social identity, or another external identity, this is a guest user we all know of and we use for the users that need to access our Azure AD)
- Internal guest (has an account in your Azure AD directory, but only has guest level to your org, they have your organization email address)
- External member (uses an external account to authenticate, but has member level access to your Azure AD, they don’t have your organization’s email address).
- Internal member (regular user inside you Azure AD we all use, has your organization email address)
These are the users that are part of the B2B collaboration feature.
There is a new B2B direct connect feature, where you set up mutual trusts between Azure ADs (probably you remember this from before as trust relationship between domains – I am old I know), so users authenticate on their Azure AD, but because of trust, they are able to access resources in your Azure AD.
Below is the table I found with an excellent explanation of UserType property, how different users authenticate and what’s their relationship to your org.
Has anybody ever used an internal guest user, and if yes what would be the appropriate use case?