Lately a lot of people love to work from home a day or two a week or if they have some kind of private obligations sometimes it is easier to access the work environment from home. To securely access your work computer or Remote Desktop Session host servers in your company data-center Microsoft created Remote Desktop Gateway role that basically is a secure tunnel that allows you to access corporate servers.
Installation of the RD Gateway server was more or less straight forward in Windows Server 2008. In windows server 2012 R2 seems the things are pretty complicated. I must admit I am using Windows server for every day operations and Remote Desktop Sessions Host role installation is my daily job. I can say that at least once a day I deploy one Remote Desktop Session host role that is used mostly for testing :-)
So I will describe here how to deploy simple Remote Desktop Gateway on the Windows Server 2012 R2, with most of the default settings that will allow all to connect through the gateway. In case you will want to tweak permissions you can play with the settings by yourself, this is only quick guide for installing Remote Desktop Gateway role on the Windows Server 2012 R2.
I don’t have a farm of RD session host servers sitting behind and I don’t want to deploy Connection broker, web access and session host server (e.g. complete infrastructure) I just want to have RD Gateway server. The things can get pretty complicated here because in the server manager you won’t have a nice icon where you can click on the green add RD Gateway server role icon and do everything through the wizard. SO I will help you out to deploy standalone RD Gateway role on the Windows Server 2012 R2.
- Open server manager and select add servers roles and features
- Nothing special on the before you begin step, just click next
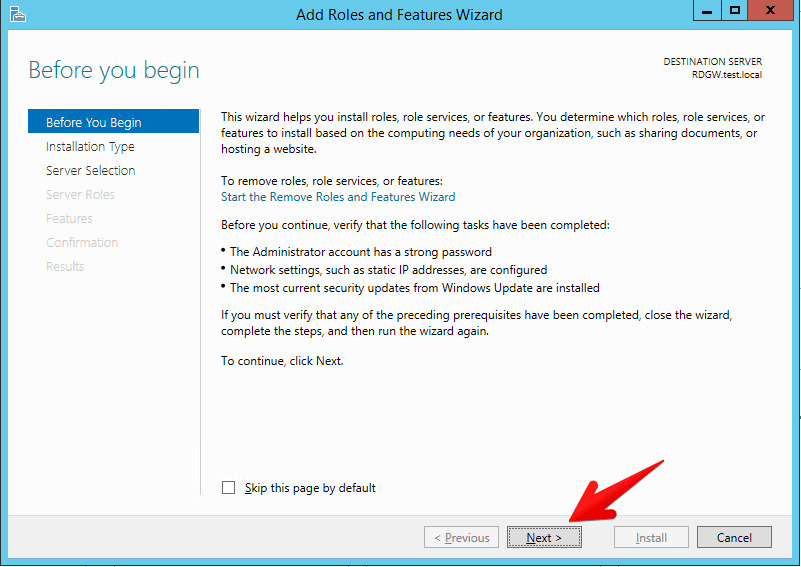
- It is important to select role based installation here. In case you select Remote Desktop Services installation wizard will lead you through Remote Desktop connection broker, web access and remote desktop session host installation which we don’t want in this simple scenario.
- On the server selection select your server that will host the Remote Desktop Gateway role
- Select Remote Desktop Services role
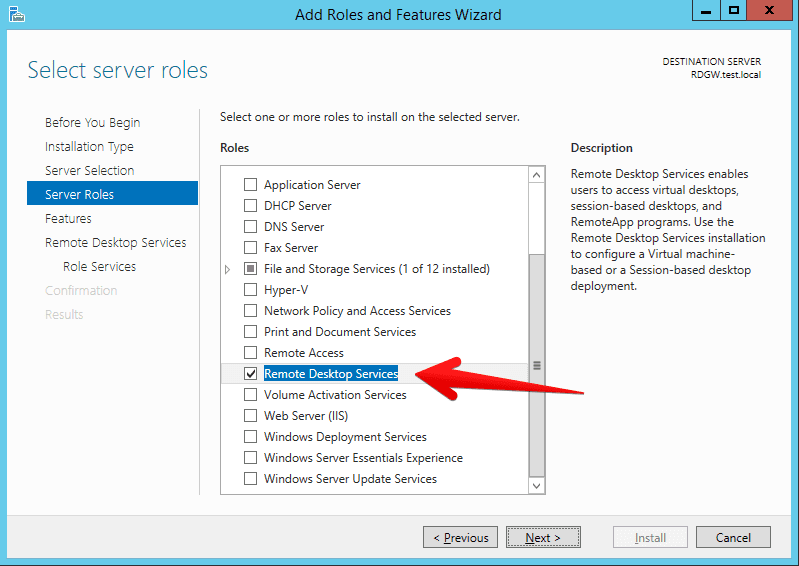
- You can skip feature if you don’t need any
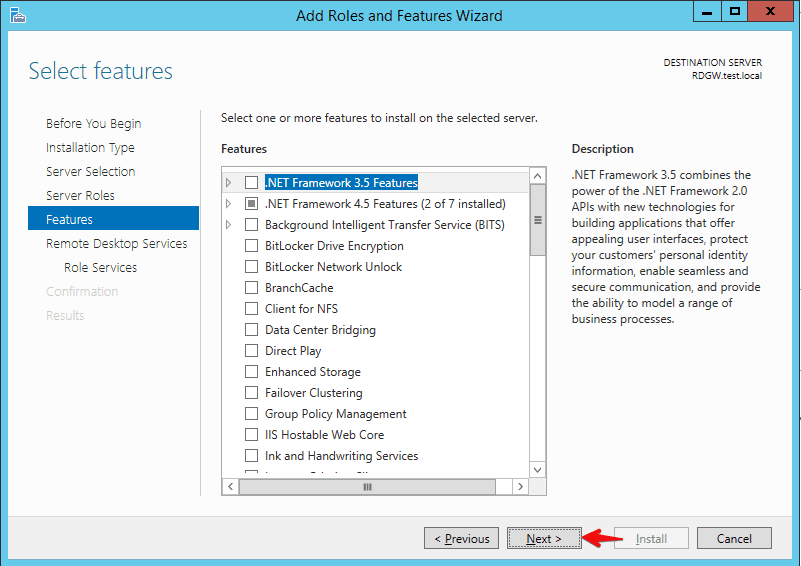
- On the Remote Desktop Services role you can just click next
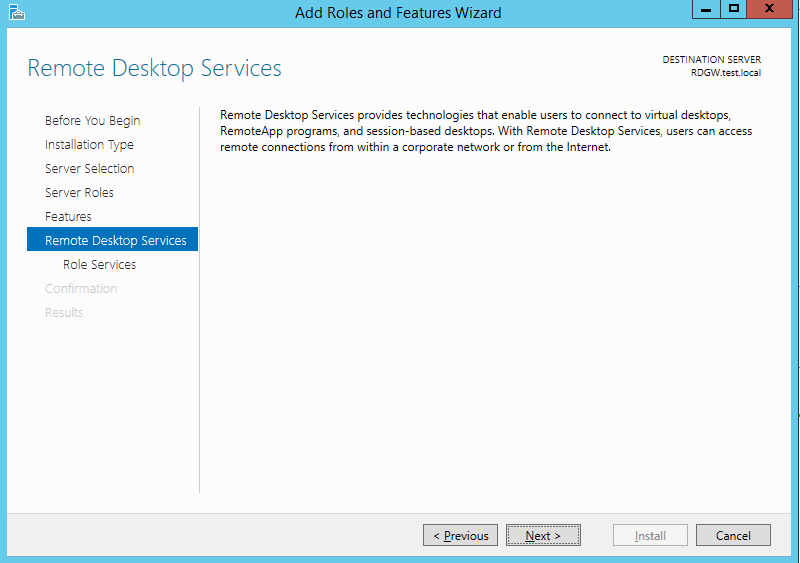
- And at last you are now on the step where you will select Remote Desktop Gateway role. Click on that role and in next dialog just click add features because Windows server will need to add additional features like Network Policy and Access services, management for the Network policy and access, the same for the RD gateway etc… Just click add features.
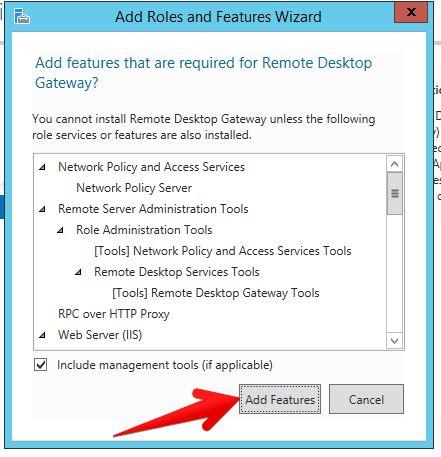
- Make sure RD Gateway role is selected and click next
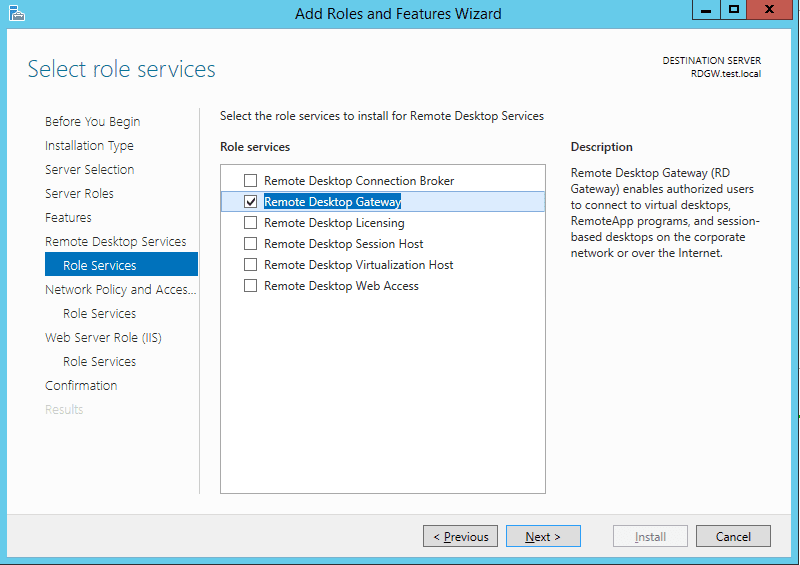
- It will inform you now about NPS access click next
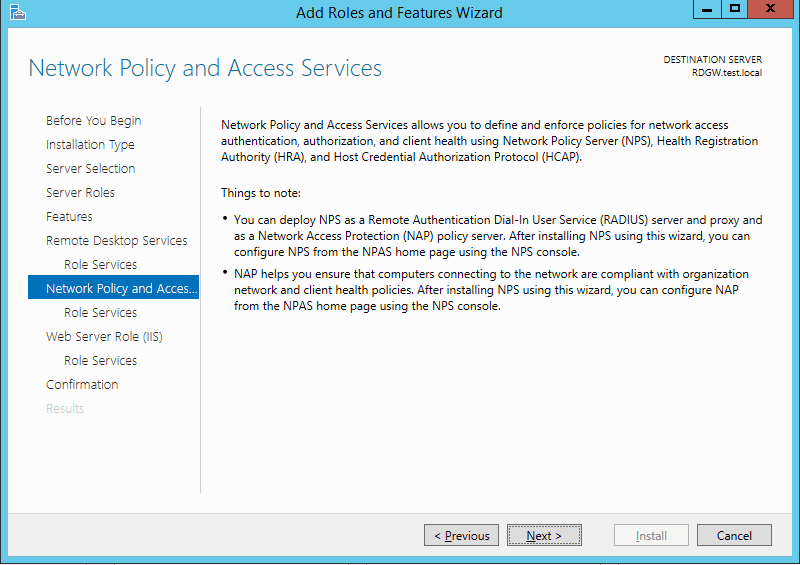
- Information that NPS policy Server will be installed
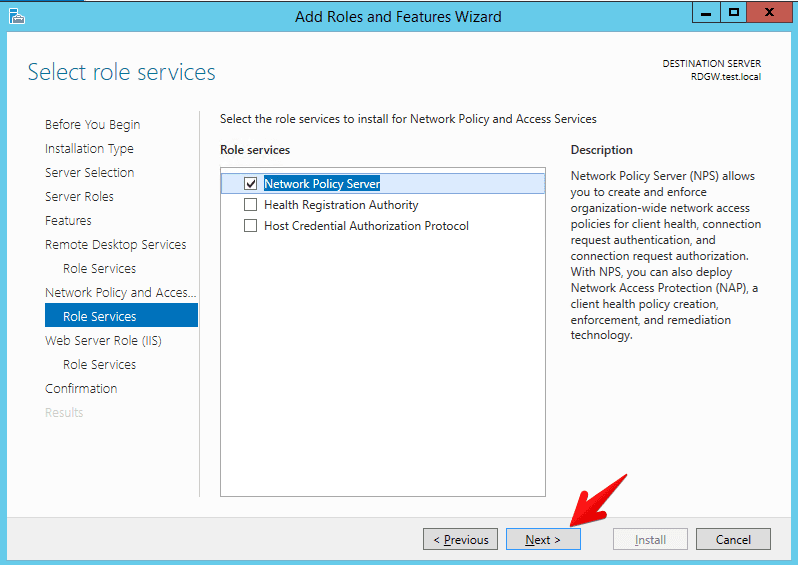
- Informational message that IIS will be deployed as well
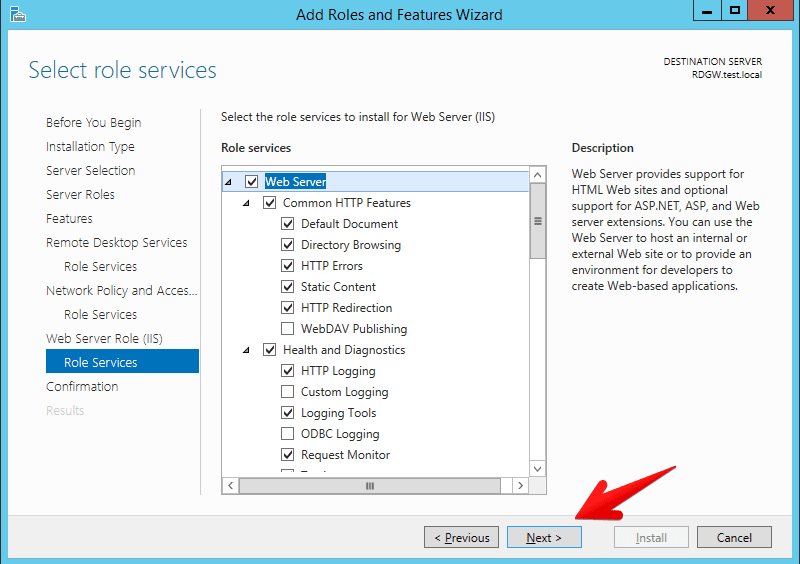
- Confirmation that RD gateway together with other required services will be installed. I checked the restart check-box just in case something else was pending for the restart
- And voila! Installation starts
- After installation is finished you go back to the server manager and click on the remote desktop services role that was just installed. When you click on the overview you will see a message: There are no RD Connection Broker servers in the server pool. This is okay since we have not deployed complete Remote Desktop Session host environment as we want to have only RD Gateway
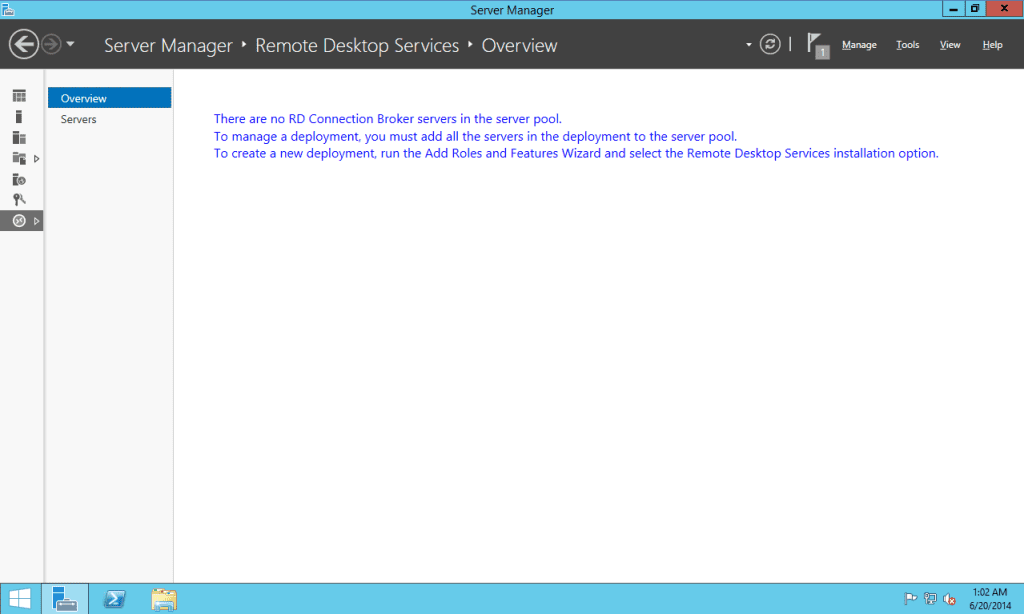
- Now go to Tools > Terminal Services > Remote Desktip Gateway Managerand you will see that our Remote Desktop Gateway server is not configured. Now most important thing for the RD Gateway is certificate, if there is no SSL certificate on the server and on the CLIENT this will not work. Certificate needs to be on the both machines in order for this to work. Other things you need to configure are Connection authorization policy (who is able to connect through the RD Gateway) and Resource authorization policy (where authenticated users will be able to connect).
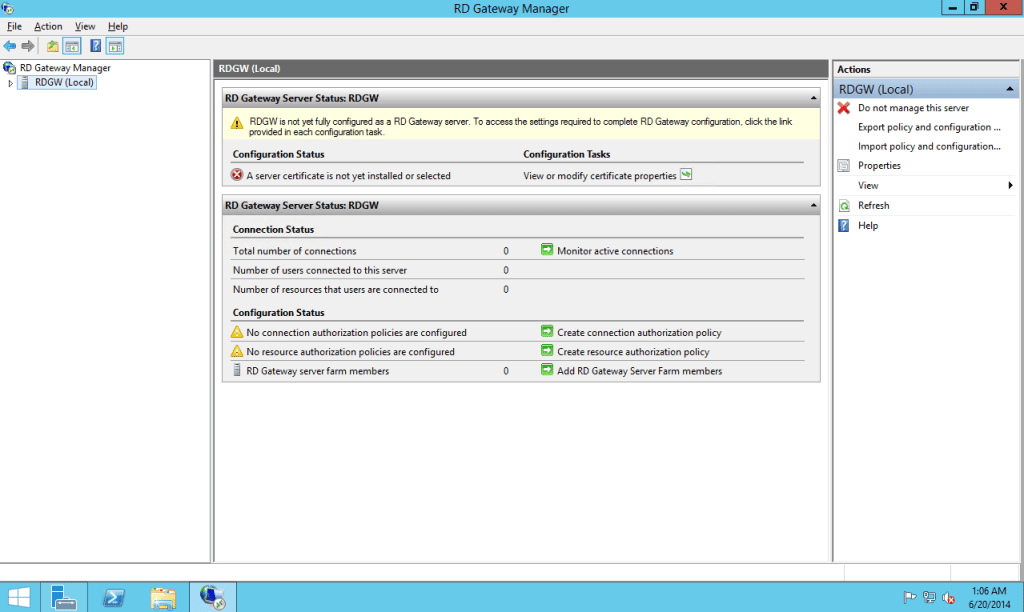
- Let’s start with the SSL certificate. Click on the view or modify certificate properties and you will see that certificate is not available.
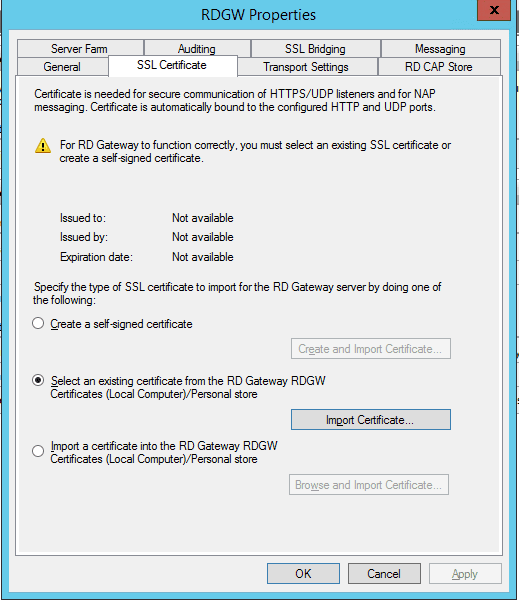
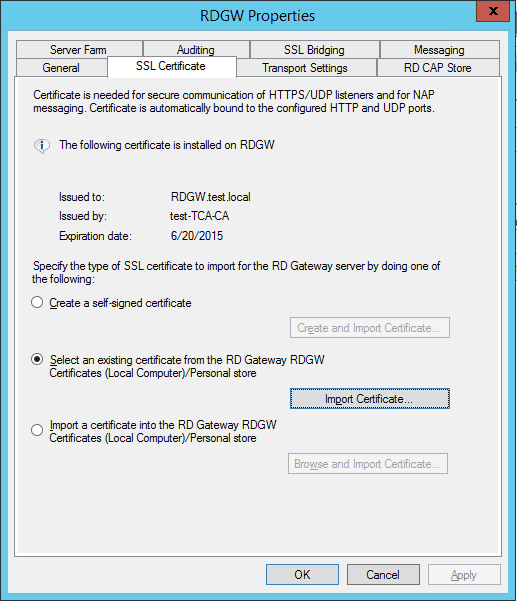
- You have multiple options now. You can create a self signed certificate on the server BUT then that self-signed certificate needs to be imported on the client. If the SSL cert is not on the client Remote Desktop Services client will not allow you to connect via the RD Gateway Server. Second is to select existing certificate which I will do in this scenario because locally we have certificate services and our internal self-signed certificates are distributed to the clients. Third is in case you have purchased certificate from third party like Symantec, Comodo or somebody else for this specific gateway you can do that as well. For tests I recommend first option, for internal ppl second option and for production where the internal and external users will connect to your infrastructure I recommend third option. The SSL certs today are really cheap so no worries about that.
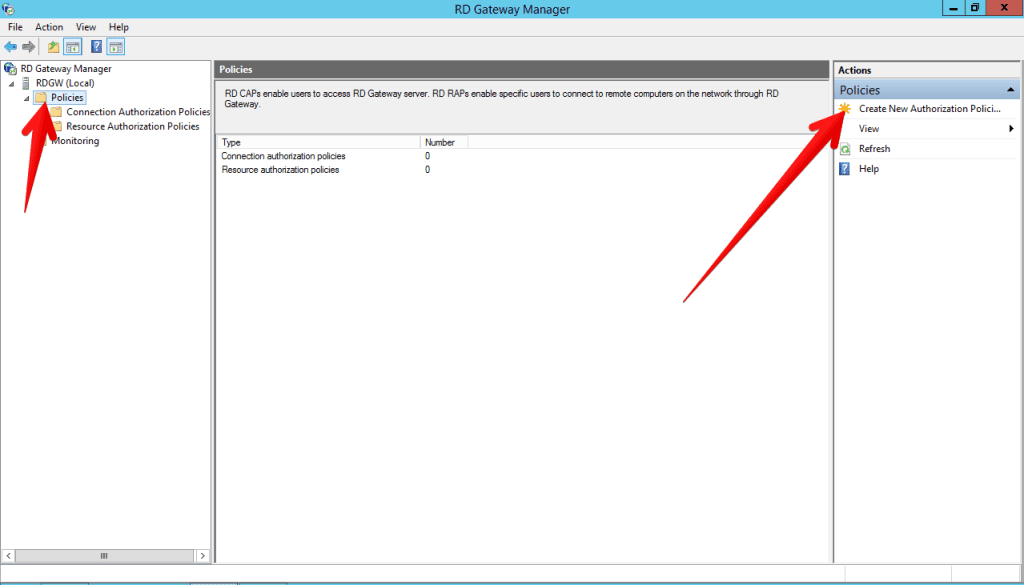
- We will continue with configuration of the RD Connection and Resource Authorization polices. The easiest way is through a simple wizard but that is hidden a bit, it was easier in the Windows 2008 R2. So go to Policies and then Create new authorization policy.
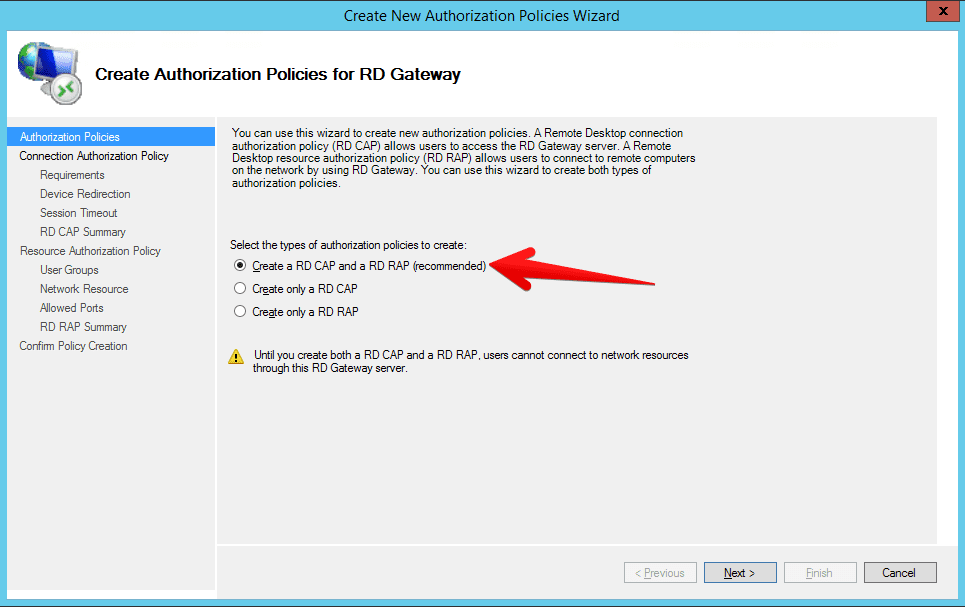
- Wizard will open and I recommend for this simple scenario selecting create RD CAP and a RD RAP policy
- Name the RD CAP policy
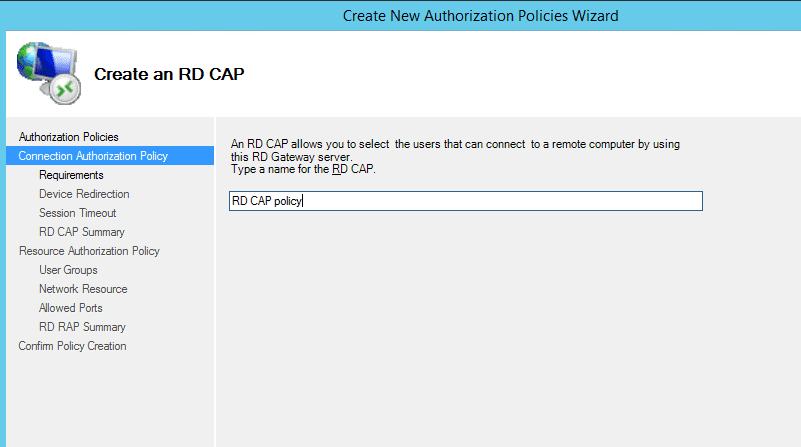
- Now you need to define who will be able to connect to the RD Gateway server. I have selected only Domain users security group but you can select whoever you want to
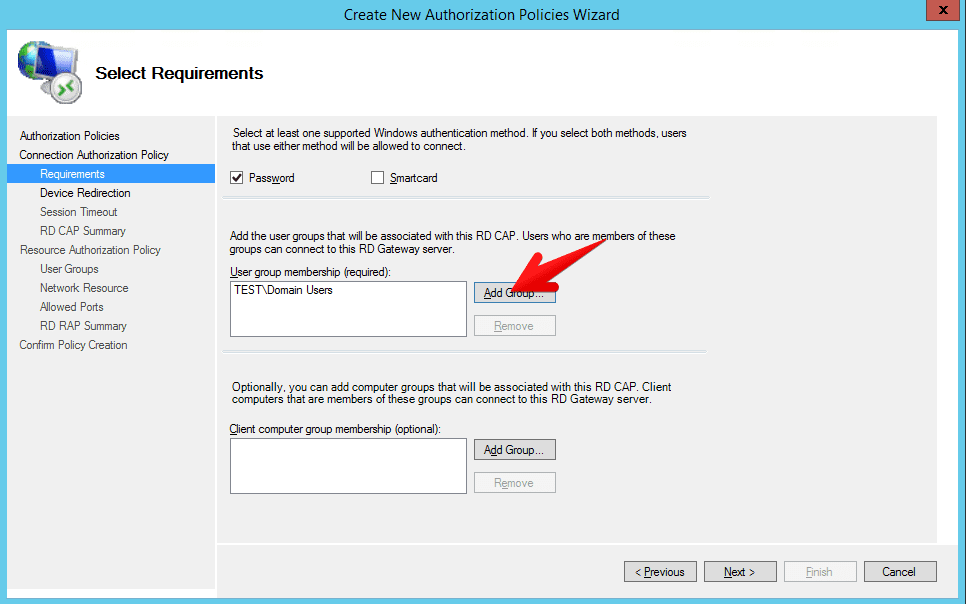
- Device redirect and session timeout I left empty currently. Basically you can select there what will be redirected from the client and after how many minutes inactive or active session will be disconnected from the RD Gateway server
- Now let’s create a RD RAP policy, name it somehow descriptive like me :P
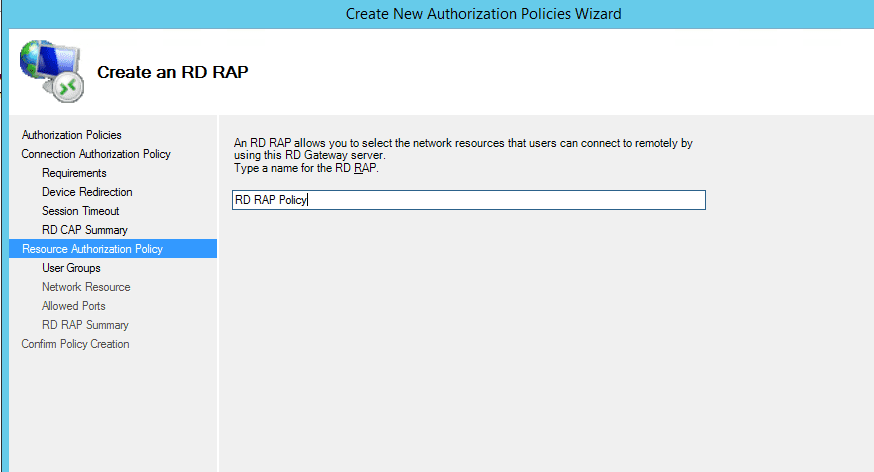
- So same user group as you selected before will be allowed to connect through the RD Gateway. Members of there groups can connect to network resources remotely through the RD Gateway. Leave as is or if you want to add somebody else as well do it now
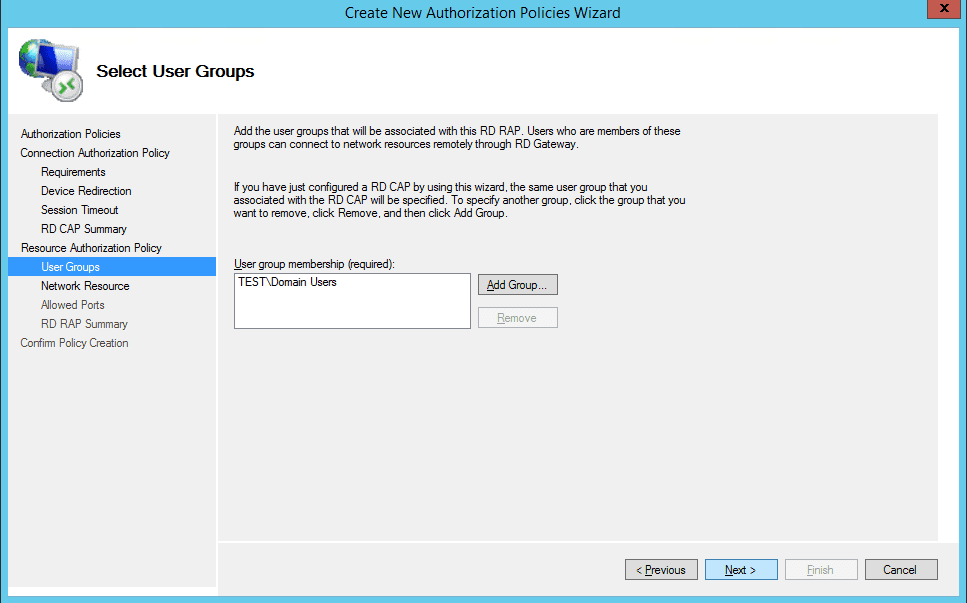
- Now you can select where the users will be able to connect to. You can select an active directory domain services network resource group, existing RD Gateway managed group or simply like me select to connect to any network resource
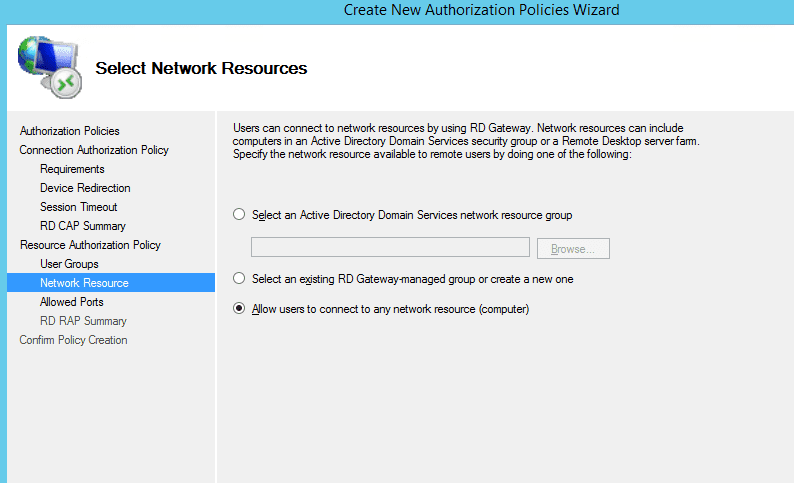
- Now select allowed ports. Default is only to port 3389 but you can define multiple separated with semi colon or just allow connections to any port
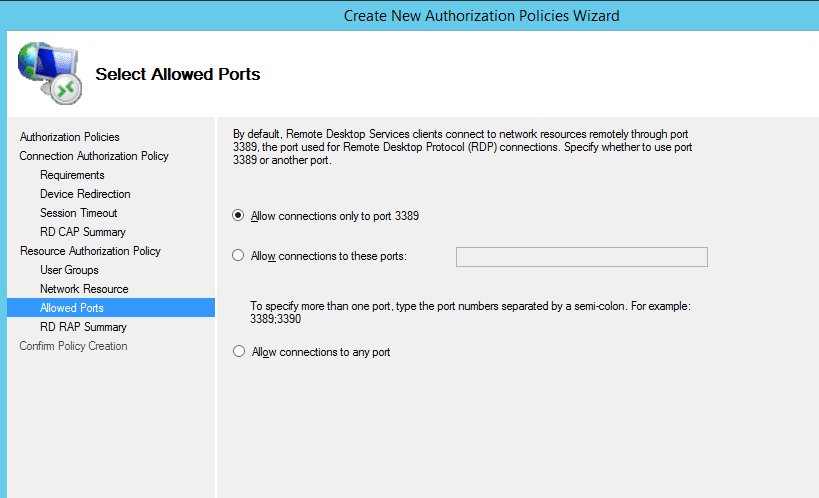
- Finish the wizard and you will receive successful message the RD RAP and RD CAP policies have been created.
- The server is now configured. Go to the client end import self-signed SSL if you used that, or if you already have SSL certificate you go to remote desktop client and then tab advanced then settings
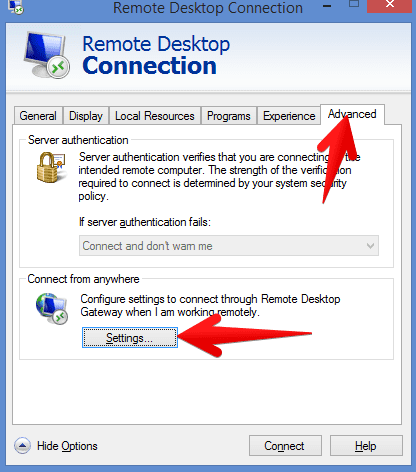
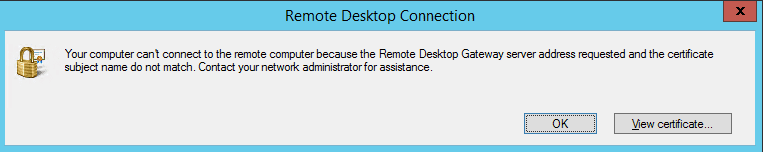
- Now specify the RD gateway server here. Please note that the RD gateway server name here and the server name on the certificate needs to be the SAME! Otherwise you will get an error below: Your computer can’t connect to the remote computer because the Remote Desktop Gateway servers address requested and the certificate subject name do not match. Contact your network administrator for assistance (YOU).
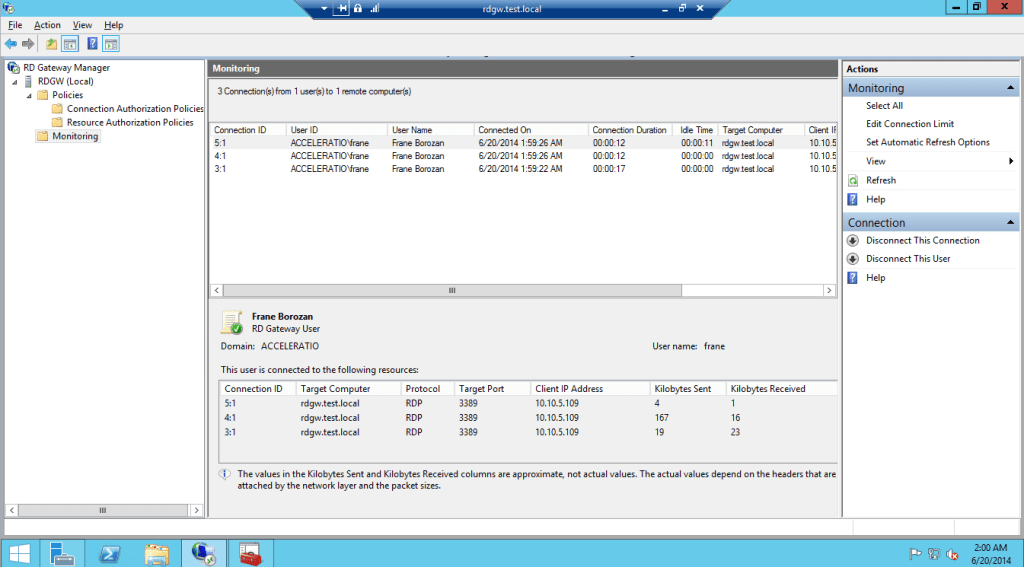
- If you followed this short how to properly and you are able to connect via the Remote Desktop Gateway in the monitoring of the Gateway you will see following. This is single user connected with three sessions, two are over UDP and one is over HTTPS. RD Gateway now also supports UDP connections when the HTTP transport is used and that is introduced in Windows Server 2012, RemoteFX uses UDP to optimize the transport of data over wide area networks.
- In case you need a log of all the users connecting through the RD Gateway you can check this software Remote Desktop Gateway Monitor. RD Gateway manager will show you only currently logged users but of course you don’t have a whole day just to sit and watch at the users, this software is cool and it will provide historical log of all the users, when they used the gateway and where they connected.

32 Responses
Were you drinking when you wrote this?
Wrong – “Remote Desktip Gateway Managerand”
Correct – “Remote Desktop Gateway Manager, and”
Haha, thanks for the info. I have not been drinking but was writing some parts fast :-)
Thanks Frane for this great tut on getting RD going on Server 2012 R2. I had been trying to work my way through it but I couldn’t quite figure out all of the steps as they are in numerous places. Your instructions are spot on and very easy to follow. Best of all…it works!
Thanks again…David
thanks David!
Good Morning
I have the following eventuality, I have a server called Server1 and another called ServerRDS.
Server1 is in the domain MYDOMINIO.COM.CO and ServerRDS is in the domain DOMINIORDS.COM.CO, these domains have no trust relationship, I need to promote Server1 as an RDS server for the domain MYDOMINIO.COM.CO, since no I have licenses to configure it, the only solution that I have at the moment is to obtain the licenses for that server from the ServerRDS server, I have a two-way connection between the servers but in the diagnosis it indicates that the credentials are not available, I give credentials DOMINIORDS.COM.CO domain and the diagnosis indicates that the connection and configuration is satisfactory, but as soon as I close the diagnostic console, the credential validation is lost and it is reconfigured again, this must be done every time I close the console of diagnosis or that session.
Additionally I cannot connect to the ServerRDS server from the RD Licensing Manager console.
Anyone know how I can solve this error?
I appreciate your kind help.
Thank you
that is not recommended scenario at least I never used it. Why you don’t split the licenses across two license servers?
Hello – great article and clearly written. I have one question – can RD Gateway used in a single server environment without a domain? I am trying to learn, just have a single server without fqdn, only let 443 through my router and I get a “Your computer cant connect to the remote computer because Remote Desktop Gateway server is temporarily unavailable”. The service is running, port 443 is open. Where should i look? Thanks
Hi Gan, I am not 100% sure lately for the all Windows server products Microsoft requires domain environment. If it is possible probably it is not supported by Microsoft so I strongly suggest to install domain controller and then to connect gateway there as well.
Hi Gan, I had the same issue. You can do so. Just edit the host file in windows\system32\drivers\host with the “IP-Address” and “Computername”.
Worked for me.
Thank you so much! I was banging my head against the wall and tearing my hair out trying to figure this out!
Hello, thanks for this great help, but… I have some problem (maybe) in the last step. I can see logon dialog to the server, but after a few sec I get a message that “Remote desktop can’t find the computer XXX…..This migrht mean that XXX does not belong to specified network. Verify… ” But the computer is a domain member, accessible by name without any problems. Any idea?
Strange. When I get to Step 22 and click Add Groups… the snap-in crashes.
Same here. Does anybody have a tip?
This is because your machine needs to be part of a domain. I had the same issue, until I created a domain on the machine. You can either make your gateway server a domain controller, or make it join an already existing domain, depending on your technical context.
If anyone is still looking for this solution – Uninstall KB3172614
Thank you for this! It’s definitely not clear how to get an RD Gateway going if you don’t want the entire kit and caboodle of Microsoft RDSHs/VDI!
It’s a shame you don’t have a donate button! I’d
definitely donate to this fantastic blog! I guess for now i’ll settle for bookmarking
and adding your RSS feed to my Google account. I look forward to brand new updates and will share this blog with my Facebook group.
Talk soon!
Have you tried this yet in 2016? Microsoft has removed all of the remaining MSCs for terminal services. I’m striving to find the PowerShell equivalent of implementing this in 2016 since there appears to be no other way to do it via gui.
To be fair, I’m doing this on server 2016 core; thought I could use RSAT on a workstation to configure after installing the rd gateway role, but I was very wrong.
Thanks for this article though. It will be a great template to do this manually.
To be honest I have not but you have inspired me to create another post that will be RD Gateway 2016 focused :-)
I look forward to the PowerShell as well it would be for sure challenge something to do via script when we were able to do everything manually :-)
I need a 2016 version of this too!
So i installed the remote desktop role on a single server using the quick setup( RD Licensing,web access,Gateway,connection broker)
all is working fine . the server that i want to grant access too is a different server (xserver) after looking though several online docs and such I decided to add the desktop role to the server I was trying to connect to (xserver). Restarted it and added it a session host.. tried to connect multiple users and it worked like it is suppose.. But now I have the RDs pop up saying i have 120 days left for the license server.. Shouldn’t the (xserver) be getting its license information form the dedicated server I have all ready installed the licensing server setup on? Do i just need to point it to my licencing server so how? Would this solution work for me? even though I have installed all services on a single server and I just want to get to (Xserver)? here is the current error that I am getting.. “There are no RD Connection Brokers server in server pool. to manage a deployment, you must add all the servers in the deployment to the server pool. To create a new deployment, run the Add Roles Wizard and Features and select the remote desktop option.. See
Steve, the easiest way to check which Licensing server you have is with PowerShell: Get-RDLicenseConfiguration
That will show you if you pointed remote desktop services to the right licensing server.
you have two ways of specifying license server for the remote desktop services (before you were able to specify it directly in the RD License manager MMC but AFAIK that doesn’t work anymore): -Mode PerUser -ConnectionBroker
1) via the group policy on the domain level you can specify the server here:
Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Licensing\
2) you can use the powershell: Set-RDLicenseConfiguration -LicenseServer
I’m a bit confused. So this is RD-Host and Gateway on the same machine? Would be what i want to achieve (else VPN), but I’ve read it’s not secure to run both on the same machine (if it’s connected to the WAN)? Further, i’ve read above but have you taken a look into Server 2016? I believe i’d manage it even without a guide, but it would be nice to know before if it even works. If not, i might need to use 2012. So anyway, thanks for the guide.
Hi Alex, of course that is true this is only generic example. The main scenario would be to have RD Gateway on the WAN forwarding traffic to the RD Host sitting behind it.
Everything works great, but my BPA gives an error on the RDS saying “The RD Gateway server must be able to contact Active Directory Domain Services”.
The RDS Server is in the domain, and can ping both the FQDN of the Domain Server and the IP of the Domain Server, as per the Technet article: https://technet.microsoft.com/en-us/library/dd320344(v=ws.10).aspx
So what could I be missing?
Do you have primary DNS on the gateway set to be DC of the domain? This leads me to domain issue, for some reason gateway is not able to resolve DC properly. Are FQDN and NETBIOS names passing the ping?
How can I login to the remote server without clicking the security policies message. I mean directly seeing the remote server desktop without being prompted to security message and click ok to see the desktop server.
This was exactly what I needed to fix RDS after a certificate mishap. Thank you.
RD Gateway Manager doesn’t show all connections. What gives?
Can you please explain what do you mean by not showing all connections?
2020 and this is exactly what I needed, thank you
Great tutorial, until the very end.
I really don’t know how to finalize the connection from the client side, totally, starting from the SSL cert (where am I suppose to import it), to the several parts of the conncetion itself (i.e., if I’m configuring a local Server , how can I configure the remote connection as if they are not on the same local subnet, etc)
thanks