CryptoLocker and its variants are ransomware viruses that re-appeared in 2013.
The crypto-virus gets around through email attachments, various browser pop-ups, and certain add-ons scattered across the internet and even hidden in background images.
There have been reports of HTML and Java Script injections as well. Those code injections exploit a web site’s vulnerabilities if it has any. Sites that are attacked usually include some kind of forum that is open to any text comments.
CryptoLocker attacks the PC and encrypts all the drivers mounted on your computer. It not only encrypts all the folders on the local drive but also attacks the file share as well. For example, it even attacks your company’s file share and your local OneDrive or Dropbox folders. It all gets encrypted.
Any experienced IT professional who has dealt with cryptolocker virus will tell you not to visit shoddy web websites—period.
OneDrive and Dropbox are not too hard to restore. Microsoft and Dropbox support file versioning so you can restore all the files that were encrypted to their previous versions. It could take some time to restore each file, but it can be done.
The biggest problem is when the cryptolocker virus attacks a company’s file share. Then it gets trickier. That happened at our company. Yes, the CryptoLocker attacked us too.
In over 90% of all small companies affected, every employee has permission to write, upload, and to edit shared files. Then you have a situation in which everyone uploads pictures, videos, and Office documents. Before you say anything, yes, we use Office 365, but our adoption level is not what it could be, and lots of users are using the file share to store Office files. It’s ridiculous, I know. They also store various .iso images that are used for software testing purposes.
The issue is that when one computer is attacked, the cryptolocker virus locks and encrypts all the files on the office’s mail file share. From there on, everything gets infected and encrypted.
If you don’t have a backup, to put it simply–you are screwed.
I mentioned that it happened to us. We were attacked by a version of the CryptoLocker last week. It attacked us internally, infecting one of the servers. We still have no clue as to how we contracted the virus but we have our SWAT team working on it as we speak.
How did we notice that the attack was taking place?
The server mounted the file share on a group policy and the CryptoLocker variant started creating .encrypt files, and leaving .txt that looked like this:
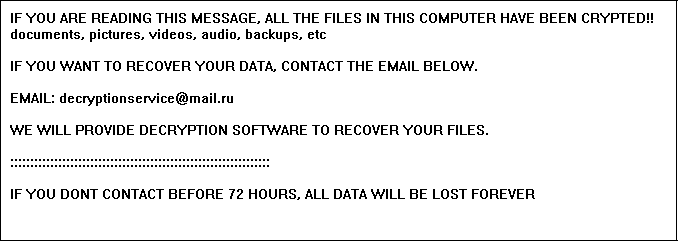
Fortunately, we monitor our servers, and when we realized what was going on, we reacted quickly. We shut down the server running the Trojan, and immediately deleted it.
We could locate the Trojan because we noticed that the CPU on one of our servers was, oddly enough, running at 100% that entire day. Servers don’t require heavy resources usage, so that was a sign that something was wrong. The Trojan encrypted just a few files that we eventually deleted since it turned out that they weren’t even important. Luckily, no important files were encrypted or damaged.
That got me thinking—what if the CryptoLocker went undetected or had enough time to encrypt the entire file share? We decided to implement a new policy that would outsmart the cryptolocker virus.
From now on, everyone in our company will have read/write permissions only on their home folder. We came up with a re-organized system:
- User folders: Each employee has a folder in which he/she stores his/her documents and stuff. The name of the employee folder is the same as the name on the domain controller, and only that employee has permissions to write to this folder.
- Design: Only designers and the marketing department have permission to read/write to this folder.
- Installations: This folder has read-only permissions for everyone employed at our company.
- Downloads: Everyone has read-only permission, except the QA team, which has read/write permissions.
- Photos: The marketing department and designers have read/write permissions, and all others have read-only permission.
With a structure like this, damage control in case of a malware infection is much easier. In fact, if one PC is infected, it will have minimal write permissions on the file share, which means that even if the malware starts encrypting files, it will encrypt some files and not the whole file share.
Of course, I’m aware that this isn’t the ultimate solution, but it does make more sense for damage control than the situation we had before. At least this way we won’t lose everything due to a malware encryption attack.
